You can also be interested in these:
- How to protect smartphones against Pegasus virus
- Which VPN is the best for android phones in 2022?
- How to change your security PIN in Samsung devices
- Why do you need cybersecurity for your router?
In the modern-day, smartphones have become an inherent part of everyday humans’ lives. They have established significant dominance in individuals’ digital habits. According to Statista, there are over 6.6 billion smartphone users globally. Statista projects this number to grow to 7.7 billion by 2027. See more particulars in the graph further down.

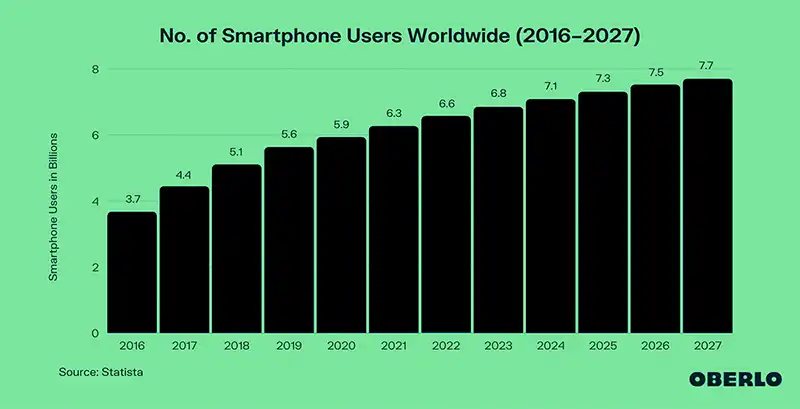
The state of smartphone and mobile App usage
The surge in smartphone usage has provided an impressive platform for mobile app developers. App developers burn their midnight oils to provide new and advanced mobile apps with different functionalities and usages.
As of 2018, the global average revenue of the mobile app market stood at $365 billion. A five-year projection by SerpWatch indicated that this number would triple to $935 billion by 2023. The increase in the global average revenue of mobile apps could be attributed to the increased usage. According to eMarketer, almost 90% of mobile app time is spent on mobile apps. As of March 2022, over 2.59 million apps were available in the Google Play Store. So many apps explain why the global average revenue derived from mobile apps and the increased overreliance on these applications by the global population.
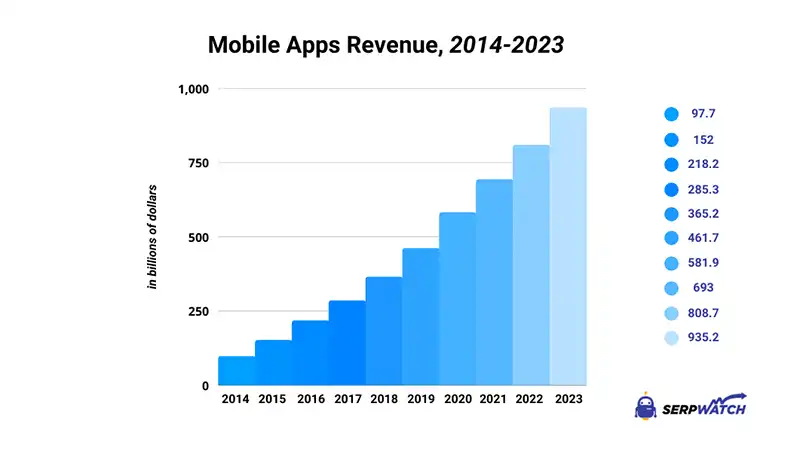
Mobile App security: The real nightmare of the mobile App market
The increased dominance of smartphones and mobile apps ushered in many security threats that target app users and their data. From a mobile app security point of view, the statistics are startling. To begin with, most organizations tend to overlook the aspect of mobile app security. According to Verizon’s 2020 Mobile Security Index, 43% of organizations completely ignored the issue of mobile app security. According to the report, organizations that sacrifice mobile app security are twice as likely to get compromised. The following statistics/facts show you how serious the issue of mobile app security is.
- Malicious mobile applications were the culprits behind over half of mobile threats in 2019
- 82% of android devices are susceptible to one or more of twenty-five vulnerabilities in the Android operating system
- Business-related mobile apps are three times more vulnerable to login credentials leakages than other mobile apps
- 95% of eCommerce mobile apps fail basic security tests
Mobile App security checklist
Comprehensively secure mobile apps are a rare sight. Although developers and app owners have a role in creating threat-free mobile apps, sophisticated hackers always have a way around the app’s security walls. A mobile app security checklist is a significant companion that can help mobile app owners and developers keep a close eye on app security. Here are the fundamental elements of the checklist.
1. Code signing certificate
Top on our checklist is the code signing certificate. The certificate is one of the most fundamental tools without which app security becomes jeopardized. Like all kinds of digital certificates, the code signing certificate is of great essence in cybersecurity. It secures codes and software scripts from access by unauthorized parties.
The most critical purpose of the code signing certificate is to let app users know that the application is genuine and from a genuine developer. To achieve its role, the certificate will shrink-wrap the mobile app and protect it against malicious editing by unauthorized intruders. Users will get to know if the code has been tampered with or altered since its publication.
In short, the code signing certificate focuses on both code integrity and legitimacy, which are essentially the basics of app security. If you want to enhance the security of your web application, you will need to buy the certificate. You do not have to spend an arm and a leg because a cheapest code signing certificate will work perfectly for you as it comes with organization validation and extended validation plans.
Although not its primary focus, the code signing certificate will also help to prevent malware distribution. Hackers usually insert malicious code into legitimate software. The repackaged code will then be introduced into the market to carry out all sorts of attacks. Such malware attacks could be detrimental to app users. But with a code signing certificate validating all code sources, it will be easy to determine if a code has been modified and infiltrated with malware.
2. Secure source codes
It will be useless to spend huge amounts of resources and extreme amounts of energy on developing a mobile app that adheres to all best security practices save for the security of the source code. It is like building a magnificent castle but failing to secure the front gate. You leave the castle open to nemesis.
From a mobile app perspective, the source code often resides on the client’s side. If this code lands in the hackers’ hands, all the hard work you put in creating the app becomes as good as dead. The best strategy here is to employ code obfuscation. This is the process of making your source code confusing and not able to be understood. With code obfuscation, it is almost impossible for attackers to reverse-engineer your code. There are many methods that are compatible with android or IOS code obfuscation. For instance, the built-in pro-guard could help with code obfuscation.
3. Strong authentications
According to Avast, 90% of passwords are vulnerable to attacks. Passwords secure app users’ accounts from access by unauthorized parties. The weaker the password, the easier it will be for a hacker to access your app data. Similarly, the stronger the password, the better it is to protect a mobile app from security threats.
But what exactly is a strong password? While creating mobile applications, developers should set guidelines that guide users when creating passwords. For instance, The application should limit the number of characters in the passwords. Moreover, the password should be required to blend all forms of characters and symbols. Such strong passwords will be a surefire way of protecting the mobile app from hackers.
But passwords are not always enough. A quick glimpse at the history of cyberattacks leads to the conclusion that, eventually, hackers always find their way around passwords. For this reason, mobile apps need to employ further authentication to boost their security. The two-step authentication has proved to be ideal for mobile apps. Two-factor authentication might exist in the form of one-time passwords, secret codes, or biometric authentication.
4. Up-to-date mobile Apps
Ensuring that all the software attached to the mobile applications are up to date is also crucial. These updates come to enhance app security and address the vulnerability or security loopholes existing in the current software. When not updated, the software can bring all sorts of security threats to your app. The best strategy is to ensure that you are using the latest app version to avoid security challenges that exist in the old app versions.
5. File and database security
The game does not end with securing the source code alone. If anything, hackers are after your source code because they want to access data. You must know that data is a valuable asset in the modern world. Data, in this case, could be critical information such as login credentials, health information, physical addresses, etcetera. This data ought to be protected at all costs. Applying encryption algorithms to ensure that database and data files are protected from unauthorized access would be a great idea.
6. Secure communications
Security risks such as man-in-the-middle attacks and snooping are common over cellular connections. Using the mobile app over WiFi could be detrimental. Such wireless connections will put you right in the jaws of attackers. To be on the safe side, it would be essential to adopt safe WiFi practices such as using virtual private networks 0r strong 4096-bit keys SSL encryption.
7. Data portability
Enabling data portability on the mobile application could be a big plus to mobile app security. Data portability is where user data is used on several platforms or services. For instance, one can use his login credentials to sign into other platforms like GitHub or StackOverflow. That way, a mobile app is able to leverage the security of more established and secure platforms without the need to implement your security protocols from scratch. The OAuth is a good protocol you could leverage when implementing data portability on your mobile app. This protocol allows one app to access a protected resource by storing the access token, thereby saving developers from the need to create their own security protocols.
8. Data backup and restore system
Even after having everything on this mobile app security checklist, your app security challenge is not solved yet. Hackers always (and I mean it) find their way into a system or app, for our case. It is for this that we have a data backup and restore system as the last (but not least) item on our checklist. Always ensure that the app has a secondary data storage system that will bail you out in case of uncertainties such as successful data breaches or loss.
Conclusion
Smartphone usage has skyrocketed. The scenario has provided ground for mobile app developers and relentless hackers who want to make a catch on the booming mobile app market. Mobile apps provide significant value to businesses, but they are also hackers’ targets. While implementing mobile apps, businesses and developers need to stick to this checklist to provide an app free from security threats.
More stories like this
- How to protect smartphones against Pegasus virus
- Which VPN is the best for android phones in 2022?
- How to change your security PIN in Samsung devices
- Why do you need cybersecurity for your router?
- IT concerns about Chrome extension security issues
- How to password protect a folder in Windows 11
